Index .
Managing Events
March 23, 2002
This tutorial is a continuation of
the Design of Vader Systems tutorial dated march 23,
2002. Introductory
tutorials are at the ontologystream web site. In Section 1 we develop a small set of
relative primes from the residue that is outside of the most active area of the
event space. In Section 2 we look at
these same objects as they are embedded in the entire event space. In Section 3, we will introduce the Remarks
feature that has just been given to the SLIPEvents browser.
This tutorial begins to explore some
essential elements from cognitive science. We see that the issues of selective focus, of
the synthetic perceptional system, are more like cognitive
science than computer science.
Real concepts and real events do not
have crisp boundaries, are sometimes diffused over time and location. We see that it is proper to regard the OSI
basic capability as the capability to create knowledge technology. And we see that it is proper to make a distinction
between information technology and knowledge technology.
Section 1: The identification of five small
SLIP relative primes
We use the same free download.
Remove all of the files and folders except the datawh.txt file.
Figure
1: The snort2.zip
contents
Use the SLIPWH.exe to develop the
conjecture
(source
port, destination IP)
by issuing the commands “a = 4”
and “b = 3”. Then issue pull
and export. Now open the
SLIPCore browser and issue commands import, extract,
and cluster 5000.
You will find that the stochastic
process will gather almost all of the atoms into one spike.
However, a transient structure will
begin with two large clusters. Issue
the Random command and the Cluster 100, to see the
two transient clusters.
Move approximately all of one of
these clusters to category B1 and the other to the category B2. One of these will cluster tightly and
quickly to a spike. The other will have
two transient clusters as in Figure 2 b.

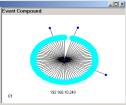
a b
Figure 2: The A1 node and the cluster from A1 that splits
In Figure 3 we see the SLIP
Framework. We have discussed the
categories B1, B2 and C1, C2 above.
However these are not what we will focus on now.
What we need is to cluster the A1
node out to about 200, use Cluster 200, in order to capture the
two large clusters and then separate the residue. Issue the command Residue after having taken the
category B1 and B2 and clicking once on the A1 node.
Figure
3: A SLIP Framework
Part of the value of this tutorial
is in showing the categorical properties of SLIP atoms. Anyway you develop the residue you will be
able to cluster this residue and find five category primes having between 6 and
10 atoms. These are indicated in Figure
3 as
{
D1’, D2, D3, D4, D5 }.
In Figure 4 we have D1’, D2, D3,
D4*, D4**, D5.
D1’ is derived from D1 to rid the
relative prime of one atom that happened to be randomly at the position of the
relative prime. This happens some
times, but by randomizing and reclustering one will separate the relative
prime. D4* and D4** are two simple
compounds that together define a prime of size 4.
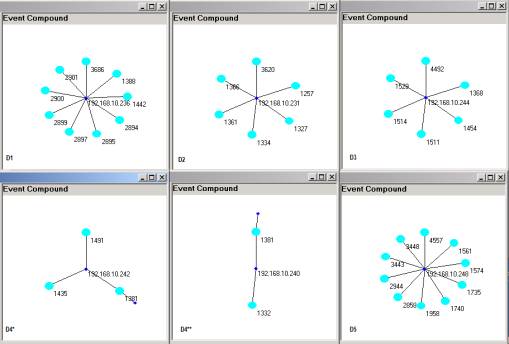
Figure
4: Five small
relative prime structures
In the table 1 we have a syntax description
of the five relative primes.
The Event Compounds in Figure 4 are
all atoms and a single relationship. If
one of the atoms has additional relationships then these are shown as an unlabeled
line with a little dark blue dot. The
only time this happens in Figure 4 is with the atom 1381. The atoms here are source ports and the
relationship types are destination IPs. One can see from D4* and D4** that the two relationships are
shared in common with the port 1381.
What about the meaning of this?
These structures are just “there”. They are in the data. Something is going on, and how we will interpret
the structure is highly dependant on personal knowledge of things that are NOT
in the data, that are not in the computer.
By leaving these interpretations out of what we expect from the computer
then we open up the interpretation to the only agent that can really make a
situated evaluation. The human bring a
vast store of memory and experience. We
bring knowledge of world events and the knowledge of a new hacker tool into a
situated judgment that something about the visual Abstraction, this morning, is
not consistent with that is normal. We
see the very beginning of a new cyber attack on the United States .mil and make
a response by sending a note and a picture to a colleague.
The computer science is restricted
to what it does best and that which a computer cannot do is left to human
perception. However, as the knowledge
base of event types develops we find more and more for the computer to do. We are surprised because a synthetic
perceptional system is seeing what ever we point our software at. The software is given computer addressable structure
and renders this as visual icons.
Table 1
D1
is developed from the pairs
{ ( x, 3686), ( x, 2901), ( x, 2900), ( x,
2899), ( x, 2897), ( x, 2895), ( x,
2894), ( x, 1442), ( x, 1388) }
where
x = 192.168.10.236.
D2
is developed from the pairs
{ ( x, 3620), ( x, 1366), ( x, 1361), ( x,
1334), ( x, 1327), ( x, 1257) }
where
x = 192.168.10.231.
D3
is developed from the pairs
{ ( x, 4492), ( x, 1529), ( x, 1514), ( x,
1511), ( x, 1454), ( x, 1368) }
where
x = 192.168.10.244.
D4
is developed from the pairs
{ x, 1491), (x, 1435), (x, 1381), (y, 1381), (y,
1332) }
where
x = 192.168.10.242 and y =
192.168.10.240.
D5
is developed from the pairs
{ ( x, 4557), ( x, 3448), ( x, 3443), ( x,
2944), ( x, 2858), ( x, 1958), ( x,
1740), ( x, 1735), ( x, 1574), ( x,
1574) }
where
x = 192.168.10.248.
The new version of the SLIP Events browser allows remarks to be developed for each simple compound and as a consequence we may share the knowledge that multiple individuals have about the meaning of the syntax. The fundamental technologies are revealed as a primitive knowledge management system. As we move into the various verticals we will see the use of this new feature.
Section 2: Embedded objects
Figure 4 shows five relative primes. The atoms that compose these relative primes were separated from the other atoms using the clustering of atoms on the circle. The identification of these specific compounds is a consequence, not of random process, but of the strengths of the hidden structure that exists in the data. So inspite of the randomness of the scatter-gather process on the circle, the same hidden structure is revealed each time, with very small variations.
A formal theory is just beginning to be discovered, and we invite others to join in this discovery. As part of this formal theory we have logic on invariance in databases and in data flow. This logic produces atoms and link-types as categories.
The key to revealing the power of this new foundational logic is the computer science. The development of software products must bring forward a deep understanding of the relationship between the
- Personal experience of knowledge,
- Selective attention facilitated by visual clues and cognitive priming and
- Communication with professional communities of practice.
The computer science helps us because the derived programs are fast, simple and astonishing. There are specific theoretical reasons why the computer science is fast and simple, and these features can be demonstrated even now.


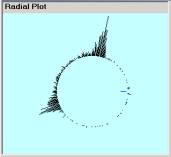
Figure 5: The embedding structure of the objects in Figure 4
Having said these things, it is important to face a reality related to how the vertical markets become capitalized.
It is not so easy to see beyond the fact that many of the future uses of visual abstraction are far more complex than is a Codd type relational database with Standard Query Language (SQL). By using the term “complexity” we indicate that there is an essential role for the human’s cognitive and recognition capability.
The complexity involved in human knowledge experience is an essential aspect of knowledge science. Without complexity we have extreme complication and expensive non-solutions to a number of important problems such as decision support and knowledge representation. The computer science is simply treated as if it can solve problems such as real time synthesis of data and tacit knowledge. The computer can facilitate visualization of category structure and this structure can serve as a communications tools as well as a process of visually priming a human’s awareness of situations.
Visual Abstraction and event Chemistry is NOT more complicated than the current Information technology.
The speed of the stochastic processes provides emergent computing and data mining type results in near real time. The output of these stochastic processes is category theory and a theory of event types. Visualizing categories is much easier than visualizing raw data. Speed and simplification open up new potential for bringing the computer into useful service.
When we compare the applications based on SQL with visualAbstraction we can only see how far visualAbstraction has to go before the applications reveal the full power of this new logic and computer science.
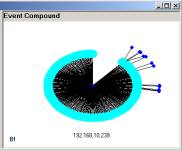
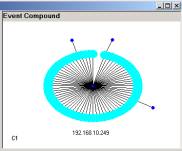
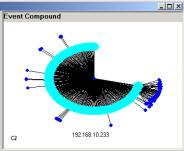
Figure 6: The three major simple event structures in our data
Formally it is easy for someone, who is comfortable with the SLIP browsers, to develop the visual objects in Figure 4, 5 and 6. In Figure 6 we have the major simple event structure that as seen in the SLIP Framework (Figure 3) as categories B1, C1 and C2.
The problem we are faced with is in how to interpret the meaning of these structures. As we start to find meaning in these simple visual Abstractions. We mature the technologies as we extend the underlying logic of the SLIP conjectures. We focus on things that are of interest in the vertical market. We render visual Abstraction objects in new ways. We use the objects as automated triggers to respond to anticipated situations. We create new types of conjecture and these new types of conjecture construct atoms and relationship-types. What we look at is changed.
Variations of the interface performance are anticipated, of course. Different verticals will deploy the SLIP technology in different ways. Often the deployment paradigm will radically restrict the access of the user to variation of the conjecture and object rendering. In this case, the right conjecture and the right rendering will have to be worked out and then some hard coding of what is not flexible will occur. This is the nature of a vertical.
The basic OSI browsers are designed to give full access to the underlying processes, except for a few essential algorithms. These algorithms are provided as complied code. Patents for the algorithms are being pursued.
Section 3: The Remark command
Knowledge experienced by an individual is shared within a community. Knowledge sharing is often expressed through the use of natural language. Visual Abstraction allows one person to find something and then send the picture and say:
Here, I have found a visual Abstraction and
this is what I think about the object.
The visual icons form a type of natural language system. However, the icons are all computer addressable and so it is proper to regard them as part of an open semiotic system of signs. These signs can be used to control computer systems and for the purpose of building shared understanding about events that are occurring. The system is open to the introduction of new sign and the modification of older signs, much in the same way a living natural language is open.
The fact that the visual Abstraction serves as a query into the original data, or into data of the same structure is nice. However, the ability to point at a picture and talk about something is very powerful. This is knowledge technology.

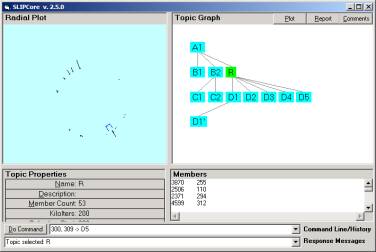
Figure 7: The new Remarks Window
The Remark window pops up into a resizable window and allows the entry of information about the concept atom or event compound that is selected in either the concept atom of event compound list.
Again, the obligation of OSI is to develop the underlying theory, to expose logic that is useful and to provide operational control over the technology through our notion of a knowledge operating system. The development of the verticals is being left to OSI Trusted Partners.
Our business plan is simple. The provision of basic capacity is developed and revealed in a development environment for each vertical. The Trusted Partner is provided support for the development environment only. However, as new features are required the development environment can be up-graded, so that the OSI Trusted Partner may satisfy client requests.
Please call OSI at 703-981-2676 if you have any comment.