Service
Link, Iterated-scatter-gather, and Parcelation (SLIP)
Technology
Short
Overview
December 16, 2001
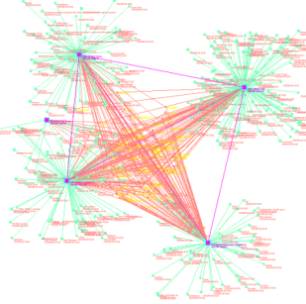
Obtaining Informational Transparency with Selective Attention
Dr. Paul S. Prueitt
President, OntologyStream Inc
December 16, 2001
Short Overview by Paul S. Prueitt, PhD, OSI Founder
703-981-2676
An exercise is available (Monday December 17th) on the first application of a SLIP Technology to full text mining.
This exercise is about the first application of a SLIP Technology to full text mining.
We begin this tutorial with an acknowledgement. Cedar Tree Software has largely been responsible for the development of three KOS (Knowledge Operating System) Browsers for OSI process architecture. Under the direction of Don Mitchell, a joint project was conceived in support of OSI’s consulting work on an Incident Management and Intrusion Detection System (IMIDS). OSI consulted with several third parties in an effort to develop a state of the art IMIDS. However, the work with Cedar Tree Software was by far the most productive.
The concept of a KOS has evolved over five months of collaboration between Mitchell and OSI Founder, Paul Prueitt. A small (< 50K) operating shell was developed to have all properties that are shared in common with the three SLIP Browsers. Commonality is also sought for a voice activated state-gesture interface between a human and a small finite state machine. The finite state machine houses a control ontology that consists of grammar, methods that delegate commands, and a response mechanism that includes visual and auditory responses. This small operating shell is called the Root_KOS.
December 2001 saw the coming to a close of the first phase of the IMIDS development work. The conclusion of the first phase renewed interest by the client in SLIP. But, unfortunately the renewed interest came at a time when end-of-year R&D budgets where being cut. OSI developed a Summary of Possibilities in order to lay out the architecture for IMIDS and to state the case that R&D should be completed and then a full deployment of the new technology made.
A pause in funding was taken as an opportunity for OSI and its partners to re-examine the processes whereby innovation is developed and then hopefully deployed. We also made an internal commitment to complete the still unfinished Event Browser. We decided to develop the software in the public view and to reveal most of the algorithmic innovations related to the use of In-memory Referential Information Bases (I-RIBs).
By December 5th, 2001 OSI had generalized the model for event log analysis and Cedar Tree quickly made these generalization available in the SLIP Warehouse and SLIP Technology Browsers. On December 7th, an exercise on importing an arbitrary event log was made available to the public.
The term "Sensor" replaced the term "Shallow" on December 10th, 2001. The new data mining technology started to be referred to as Sensor Link, Iterated-scatter-gather and Parcelation (or SLIP).
OSI’s data mining technology is based on link analysis, emergent
computing and category theory. The
first suite of software applications are used to modeling distributed in
location and time computer hacker/cracker incident events and for modeling
computer (and infrastructure) vulnerabilities. This IMIDS technology is fully
operational and available for demonstration.
A standard link relationship is definable by the user using small Browsers. Each Browser is less then 350K in size and has no installation procedure.
Patterns revealed in the link relationship are used to define location and time distributed "events". These events are visualized as clusters and then as pictures that appear like chemical compounds.
a b
Figure 1: Two elementary types exist, atoms and links
It is felt that the SLIP Technologies provide a ready to use data
mining and data visualization tools.
·
Both atoms and
links are abstractions taken from the actual data invariance that exist in the
data source. The data source is any
event audit.
·
Automated
conversion of the event chemistry to finite state transition models (colored
Petri nets) is possible. This
conversion will push automation form the Browsers into an Intrusion Detection
System (IDS) or any distributed event detection system (DEDS) such as network
trouble ticket analysis systems deployed in telecommunications infrastructure.
·
A theory of
state transition and behavioral analysis is available and is to be applied (by
OSI) to creating templated profiles of opposition activity and intentions. The social science involved is subject to a
PhD dissertation and to scholarship by members of the BCNGroup Inc, an
foundation that supports basic research on behavioral and computational
neurosciences.
A critical issue in IMIDS has to do with the prediction of events
before they occur or the identification of an event while the event is
occurring.
Human analysis based on the viewing of event chemistry will be
predictive in three ways
1) The human
will have a cognitive aid for thinking about and talking with peers about the
events and event types
2) A top down
expectancy is provided for pattern completion of partially developed event
chemistry
3) Coherency
testing separates viewpoints into distinct graphic pictures and this provides
informational transparency with a selective attention directed by user voice
commands.
Although the SLIP-I-RIB technology was developed for seven regional
Computer Emergency Response Teams (CERTs) the small Warehouse Browser will take
ANY event log, and allow the user to define any link analysis relationship. The Technology Browser produces clustered
visualization of the linkage over any small or large dataset. The Event Browser will produce two layers
of event chemistry in correspondence to event atoms and event compounds. The Enterprise IMIDS (under development
now) will push small mobile automation controllers (stand alone programs) from
the desktop into Distributed (IDS) and DEDS components.
In early December 2001, Mitchell and Prueitt spent a few days talking
about the computer science based on .NET Visual Basic and C# and theoretical
work based on a model of diffusion processes.
The notes from this discussion are available in the first exercise on
the event browser (part 2).
SLIP is complementary to knowledge-based systems. OSI is able to deploy a chosen knowledge
sharing system and the SLIP-I-RIB technology using a deployment compliance
model under development. Any one of
several enterprise knowledge sharing systems are readily deployable along with
the SLIP-I-RIB technology.
A process model for any such deployment has been under development. The
process model is simpler than the SW-CMM model for software procurement, and
reflects modern Knowledge Management practices, developed at George Washington
University and by several leading process theorists.
OSI has long had a interest in developing a SW-CMM type compliance model for the adoption of knowledge technologies. In 1990, SW-CMM was put forward as a Business Process Re-engineering type model to govern government procurement of software. This model has evolved to where it now governs quite a lot of the Federal government’s acquisition of software and software consulting services.
We propose that the sponsorship of basic innovation in knowledge technology is not as functional as our social needs would require. A process model for the development of knowledge technology innovation is needed. The development and deployment of SLIP-I-RIB Technologies is following such a process model.